Test na instalatsiiata
Sled kato sme instalirali
ueb survur Apache 2, konfigurirali sme nastroikite na SSL, suzdali
sme self-signed sertifikat, kakto i testova ueb stranitsa –
vreme e da testvame konfiguratsiiata si:
/usr/local/apache2/bin/apachectl startssl
Apache/2.0.52 mod_ssl/2.0.52 (Pass Phrase Dialog)
Some of your private key files are encrypted for security reasons.
In order to read them you have to provide us with the pass phrases.
Server 127.0.0.1:443 (RSA)
Enter pass phrase:*************
Ok: Pass Phrase Dialog successful.
Sled kato startirame
survura triabva da se opitame da izvurshim konektsiia kum nego, kato
estestveno mu ukazhem, che bihme zhelali vruzkata kum nego da minava
prez kriptiran “tunel”.
Elementarno – ueb
brauzer i vuvezhdame https://name.of.the.web.server (v
posocheniia primer https://www.seccure.lab)
Purvoto, koeto shte vidite
(sled kato natisnete Enter) e Warning Message na brauzera, koeto vi
informira za tova, che ima problem pri avtentikatsiiata na ueb survura,
do koito iskame da dostignem.
V sledvashtata figura e
pokazan primer s MS Internet Explorer 6.0.

Napulno normalno. Tozi
prozorets se poiavava zashtoto:
Sertifikata
na ueb survura ne e podpisan ot root CA ili drug dostoveren CA
suruvr;
I vtoro - CN (Common
Name) atributa na sertifikata NE otgovaria na imeto na ueb saita. Ako
ste oburnali vnimanie v CHast II na statiiata, pri suzdavaneto na
sertifikata zadadohme stoinost "Test-Only Certificate". Za
CN e prieto da se zadava FQDN (Fully Qualified Domain Name) –
pulnoto domein ime na saita (v primera www.seccure.lab)
Za sega shte natisnem butona
Yes i ako vsichko ostanalo e nared bi triabvalo da vidite sledvashtiia
ekran:
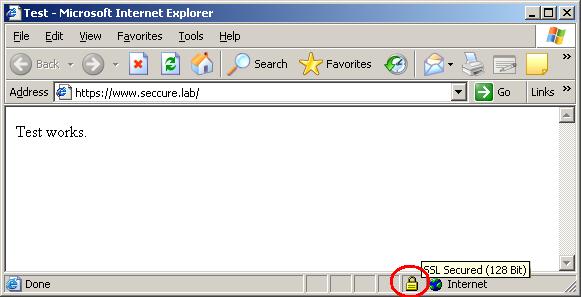
Oburnete vnimanie, che v
status bar na brauzura se e poiavila nova ikonka (ogradena v cherveno),
koeto oznachava, che kriptirana vruzka sus survura e ustanovena
uspeshno. Stoinostta "128-bit" vi informira za tova che
simetrichniia klyuch, izpolzvasht se za dekriptirane na dannite e s dulzhina
128 bita, koeto e predostatuchno (v nashiia sluchai) za da zashtiti trafika
ot neotoriziran dostup.
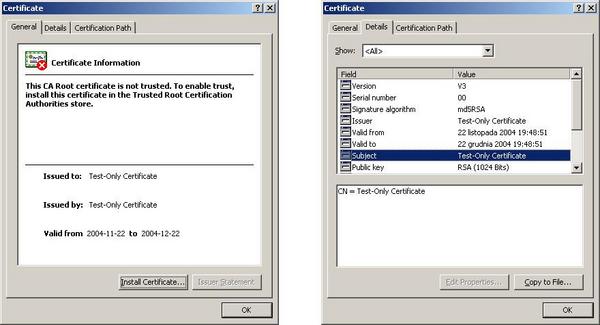
Ako kliknete dva puti
vurhu “katinarcheto” shte vidite detailna informatsiia za
sertifikata na ueb survura, kakto e pokazano:
Troubleshooting (koeto
obiknovenno se prevezhda kato “proizvodstvena avariia”)
Ako po niakakva prichina ne
mozhe da dostignete do ueb saita, ima edin dobur instrumen, koito se
kazva "s_client" i e vklyuchen biliotekite na OpenSSL. S
pomoshtta na s_client mozhe da izvurshite diagnostika na TLS/SSL
konektsiiata. V primera e pokazano kak stava tova:
/usr/bin/openssl s_client -connect localhost:443
CONNECTED(00000003)
depth=0 /CN=Test-Only Certificate
verify error:num=18:self signed certificate
verify return:1
depth=0 /CN=Test-Only Certificate
verify return:1
---
Certificate chain
0 s:/CN=Test-Only Certificate
i:/CN=Test-Only Certificate
---
Server certificate
-----BEGIN CERTIFICATE-----
MIICLzCCAZigAwIBAgIBADANBgkqhkiG9w0BAQQFADAgMR4wHAYDVQQDExVUZXN0
LU9ubHkgQ2VydGlmaWNhdGUwHhcNMDQxMTIyMTg0ODUxWhcNMDQxMjIyMTg0ODUx
WjAgMR4wHAYDVQQDExVUZXN0LU9ubHkgQ2VydGlmaWNhdGUwgZ8wDQYJKoZIhvcN
AQEBBQADgY0AMIGJAoGBAMEttnihJ7JpksdToPi5ZVGcssUbHn/G+4G43OiLhP0i
KvYuqNxBkSqqM1AanR0BFVEtVCSuq8KS9LLRdQLJ/B1UTMOGz1Pb14WGsVJS+38D
LdLEFaCyfkjNKnUgeKMyzsdhZ52pF9febB+d8cLmvXFve28sTIxLCUK7l4rjT3Xl
AgMBAAGjeTB3MB0GA1UdDgQWBBQ50isUEV6uFPZ0L4RbRm41+i1CpTBIBgNVHSME
QTA/gBQ50isUEV6uFPZ0L4RbRm41+i1CpaEkpCIwIDEeMBwGA1UEAxMVVGVzdC1P
bmx5IENlcnRpZmljYXRlggEAMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQEEBQAD
gYEAThyofbK3hg8AJXbAUD6w6+mz6dwsBmcTWLvYtLQUh86B0zWnVxzSLDmwgdUB
NxfJ7yfo0PkqNnjHfvnb5W07GcfGgLx5/U3iUROObYlwKlr6tQzMoysNQ/YtN3pp
52sGsqaOOWpYlAGOaM8j57Nv/eXogQnDRT0txXqoVEbunmM=
-----END CERTIFICATE-----
subject=/CN=Test-Only Certificate
issuer=/CN=Test-Only Certificate
---
No client certificate CA names sent
---
SSL handshake has read 1143 bytes and written 362 bytes
---
New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-SHA
Server public key is 1024 bit
SSL-Session:
Protocol : SSLv3
Cipher : DHE-RSA-AES256-SHA
Session-ID: 56EA68A5750511917CC42A1B134A8F218C27C9C0241C35C53977A2A8BBB9986A
Session-ID-ctx:
Master-Key: 303B60D625B020280F5F346AB00F8A61A7C4BEA707DFA0ED8D2F52371F8C4F087FB6EFFC02CE3B48F912D2C8929DB5BE
Key-Arg : None
Start Time: 1101164382
Timeout : 300 (sec)
Verify return code: 18 (self signed certificate)
---
GET / HTTP/1.0
HTTP/1.1 200 OK
Date: Mon, 22 Nov 2004 22:59:56 GMT
Server: Apache
Last-Modified: Mon, 22 Nov 2004 17:24:56 GMT
ETag: "5c911-46-229c0a00"
Accept-Ranges: bytes
Content-Length: 70
Connection: close
Content-Type: text/html
TestTest works.
closed
s_client ima dosta polezni
optsii, kato naprimer vklyuchvane/izklyuchvane poddruzhkata na protokoli
(-ssl2, -ssl3, -tls1), izpolzvane na siguren shifur (-cipher),
ustanoviavane v rezhim debug (-debug), sledene na sustoianieto i
suobshteniiata na SSL/TLS konektsiiata (-state, -msg), kakto i niakoi drugi
optsii koito mozhe da vidite v helpa na s_client, i koito mozhe da vi
budat polezni.
Ako s pomoshtta na s_client
ne uspeete da otkriete problema, shte triabva da promenite stoinostta na
LogLevel (v httpd.conf) na "debug", restartiraite Apache i
sled tova proverete logovete (/usr/local/apache2/logs/) za poveche
informatsiia.
Mozhe sushto taka da opitate
i s niakoi drugi instrumenti, kato naprimer Ethereal
ili ssldump.
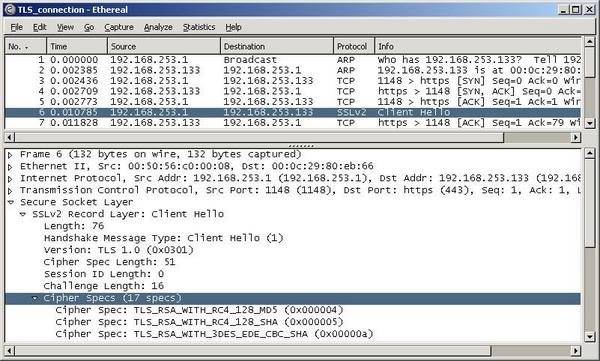
Blagodarenie na tezi instrumenti, mozhe pasivno da nablyudavate
SSL-rukostiskane (SSL Handshake) i eventualno da razberete kakva e
prichinata za problema. Na sledvashtata figura mozhe da vidite skriinshot
na SSL rukostiskane nablyudavano s Ethereal.
Iskrenoto mi zhelanie beshe tazi
chast na statiiata da bude posledna, no se okaza, che ne sum pretsenil
pravilno razpredelenieto na materiala i ako vsichko bude publikuvano
tuk, ima opasnost tazi chast da stane dosadno dulga i trudna za
chetene. Blagodaria na chitatelite za kritikite i komentarite na purvite
dve chasti! Predvaritelno blagodaria i za turpenieto Vi!
V poslednata chast (obeshtavam da e
posledna) shte vidite “obeshtanite” preporuchitelni nastroiki,
a sushto taka (lichni blagodarnosti na Veso)
shte zasegnem i temata za sertifikatite, poluchavane na sertifikat ot
dostoveren CA survur, kakto i vuzmozhnost za poluchavane na sertifikat
ot lokalen CA.

